eduffield
Core Developer
It’s a well known fact that the anonymity of Bitcoin is trivial to break, and many projects have started with an intention to bring anonymity to digital currency to protect consumers and businesses.
Darkcoin is the first privacy-centric digital currency. Founded in 2014, Darkcoin uses its anonymizing technology called Darksend to keep users funds safe and make the blockchain protected for everyday use without being tracked at some point in the future. Darksend uses a 2-tier network known as the masternode network to provide mixing services. Utilizing this technology, users are able to achieve a high level of anonymity. Darksend is trustless, decentralized and it’s nearly free to use.
CoinShuffle and Darkwallet are new technologies targeted at providing anonymity on the Bitcoin network. CoinShuffle was created by researchers from Saarland University. Included were Tim Ruffing, Pedro Moreno-Sanchez, and Aniket Kate. Their paper can be found at http://crypsys.mmci.uni-saarland.de/projects/CoinShuffle/coinshuffle.pdf.
DarkWallet was created in 2013 by Amir Taaki and Cody Wilson, but has since been adopted by a group of open source programmers.
The problem with CoinShuffle arises from the need to return change to the participants. Change has to be handled with the greatest of care in situations where anonymity is important. Change is very important because it can expose anonymized transactions if dealt with incorrectly. This can happen by observing what is done with the change after doing the anonymous transaction.
When making anonymity technology, one must remember the blockchain can be traced bi-directionally. These vulnerabilities come from the fact that, if you anonymize 1BTC at a point, then you spend some of it, later on that change must be kept separate from any identifiable transactions. Otherwise you can simply walk backward through the transactions from the identifiable transaction, to the transaction meant to be anonymous.
From the paper:
“The use of change addresses is supported in CoinShuffle: Participants can announce additional change addresses in phase 1, if they do not have an address holding exactly the mixing amount B ν. In phase 5, every participant adds all the change addresses as outputs of the mixing transaction tx before it is signed. CoinShuffle still preserves the unlinkability between the input addresses and the (regular) output addresses of the honest participants.”
There are 2 connected issues with the mismanagement of change. Mario Müller (DarkcoinTalk user Aswan) originally found this issue in Darksend. Presently, this has been resolved in Darksend and it is not vulnerable these kind of attacks.
1. CoinShuffle Vulnerability
Forward Change Linking:

In this example, Alice anonymizes 1.2BTC, which goes to 2 outputs, 1BTC and 0.2BTC. She then spends .7BTC from the 1BTC output, receiving change of 0.3BTC. That 0.3BTC then goes to an identifiable source, confirming Alice also spent the .7BTC in the prior transaction.
To identify the sender of the anonymous transaction, start at the “coinbase” transaction and go backwards in the blockchain till you get to the “Alice sends 0.7BTC anonymously”. As coinbase, you know it was your user who just recently bought something anonymously, thus breaking the anonymity completely.
Through Change Linking:
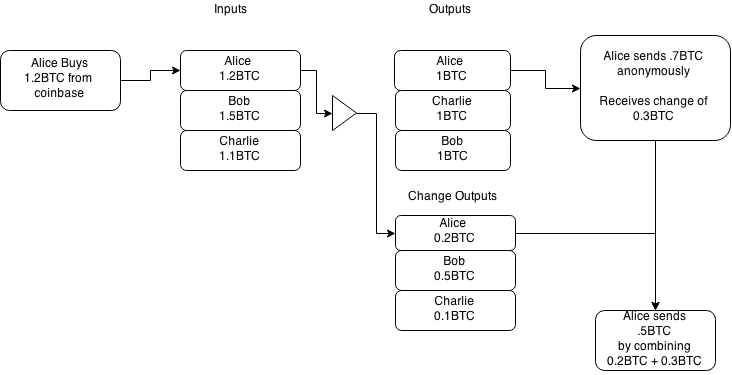
In the second example, Alice buys 1.2 BTC from coinbase, then anonymizes this amount into a 1BTC output. She then spends the 1BTC, receives change in the amount of 0.3BTC and then combines that with her 0.2BTC earlier change.
By combining the change from the anonymous transaction (0.3BTC) and the change she received from the CoinShuffle transaction, you can link the entire history before and after, completely breaking the anonymity.
Solution:
All issues presented here can be solved, but require denominated inputs and outputs. Just like the United States Dollar, which has denominations of $1, $5, $10 and $20, Darksend uses 0.1DRK, 1DRK, 10DRK and 100DRK. When mixing on the network, users can only send and receive these denominations. Afterward, transactions are protected by combining the denominations to pay slightly over the required amount.
For example, if a user needs to pay 1.17DRK anonymously, they will use 1DRK + 0.1DRK + 0.1DRK. This results in a transaction that pays exactly 1.17DRK to the payee, and pays a mining fee of 0.03DRK to eliminate change related tracking.
3. DarkWallet Vulnerability : Uniquely identifiable amounts
This mixer is constructed in such a way, where multiple users (or idle mixing bots) are paired up with users desiring to send funds in real time. It’s trivial to de-anonymize any transaction used in DarkWallet due to the unique values of the amounts in the transactions.

For Example:
In this transaction, 0.05BTC was sent through the mixer. To identify the source of the money, one simply has to add up the values on the right until they match one of the values on the left.
0.05+0.0499+0.0001(fee) = 0.10BTC.
0.0499+0.05940182+0.0001(fee) = 0.10940182BTC.
This gets exponentially more difficult as more users are added to the mixer. However, these sessions can be retroactively de-anonymized at any point in the future.
Transactions involved:
https://blockchain.info/tx/4eb3b2f9fe597d0aef6e43b58bbaa7b8fb727e645fa89f922952f3e57ee6d603
https://blockchain.info/tx/1694122b34c8543d01ad422ce600d59f8d8fde495ac9ddd894edc7139aed7617
Solution:
There is no known solution to this issue.
4. CoinShuffle and DarkWallet Vulnerability : DOS attack
Both Coinshuffle and Darkwallet are susceptible to DOS attacks, where a malicious user simply refuses to sign the final transaction or logs off during one of the final phases. Since a signature is required to successfully make the final transaction, this process can be stopped simply by refusing to participate.
Darkwallet and CoinShuffle have suggested a few different approaches to solve this, but all of these allow initial attacks to take place on the network before some action can be taken to protect the network further.
Solution:
Darksend uses a novel approach to protect the network from attack known as a collateral transaction. When opening a new mixing session, the user must make out a complete and signed transaction to the masternode he wishes to mix on. Once the process begins, the user is then obligated to complete the process by responding to requests and completing the mixing session or else the collateral transaction will be cashed. This can be thought of as putting a deposit down on a lease, afterward you retain your money if you acted according to the contract.
Darkcoin is the first privacy-centric digital currency. Founded in 2014, Darkcoin uses its anonymizing technology called Darksend to keep users funds safe and make the blockchain protected for everyday use without being tracked at some point in the future. Darksend uses a 2-tier network known as the masternode network to provide mixing services. Utilizing this technology, users are able to achieve a high level of anonymity. Darksend is trustless, decentralized and it’s nearly free to use.
CoinShuffle and Darkwallet are new technologies targeted at providing anonymity on the Bitcoin network. CoinShuffle was created by researchers from Saarland University. Included were Tim Ruffing, Pedro Moreno-Sanchez, and Aniket Kate. Their paper can be found at http://crypsys.mmci.uni-saarland.de/projects/CoinShuffle/coinshuffle.pdf.
DarkWallet was created in 2013 by Amir Taaki and Cody Wilson, but has since been adopted by a group of open source programmers.
The problem with CoinShuffle arises from the need to return change to the participants. Change has to be handled with the greatest of care in situations where anonymity is important. Change is very important because it can expose anonymized transactions if dealt with incorrectly. This can happen by observing what is done with the change after doing the anonymous transaction.
When making anonymity technology, one must remember the blockchain can be traced bi-directionally. These vulnerabilities come from the fact that, if you anonymize 1BTC at a point, then you spend some of it, later on that change must be kept separate from any identifiable transactions. Otherwise you can simply walk backward through the transactions from the identifiable transaction, to the transaction meant to be anonymous.
From the paper:
“The use of change addresses is supported in CoinShuffle: Participants can announce additional change addresses in phase 1, if they do not have an address holding exactly the mixing amount B ν. In phase 5, every participant adds all the change addresses as outputs of the mixing transaction tx before it is signed. CoinShuffle still preserves the unlinkability between the input addresses and the (regular) output addresses of the honest participants.”
There are 2 connected issues with the mismanagement of change. Mario Müller (DarkcoinTalk user Aswan) originally found this issue in Darksend. Presently, this has been resolved in Darksend and it is not vulnerable these kind of attacks.
1. CoinShuffle Vulnerability
Forward Change Linking:
In this example, Alice anonymizes 1.2BTC, which goes to 2 outputs, 1BTC and 0.2BTC. She then spends .7BTC from the 1BTC output, receiving change of 0.3BTC. That 0.3BTC then goes to an identifiable source, confirming Alice also spent the .7BTC in the prior transaction.
To identify the sender of the anonymous transaction, start at the “coinbase” transaction and go backwards in the blockchain till you get to the “Alice sends 0.7BTC anonymously”. As coinbase, you know it was your user who just recently bought something anonymously, thus breaking the anonymity completely.
Through Change Linking:
In the second example, Alice buys 1.2 BTC from coinbase, then anonymizes this amount into a 1BTC output. She then spends the 1BTC, receives change in the amount of 0.3BTC and then combines that with her 0.2BTC earlier change.
By combining the change from the anonymous transaction (0.3BTC) and the change she received from the CoinShuffle transaction, you can link the entire history before and after, completely breaking the anonymity.
Solution:
All issues presented here can be solved, but require denominated inputs and outputs. Just like the United States Dollar, which has denominations of $1, $5, $10 and $20, Darksend uses 0.1DRK, 1DRK, 10DRK and 100DRK. When mixing on the network, users can only send and receive these denominations. Afterward, transactions are protected by combining the denominations to pay slightly over the required amount.
For example, if a user needs to pay 1.17DRK anonymously, they will use 1DRK + 0.1DRK + 0.1DRK. This results in a transaction that pays exactly 1.17DRK to the payee, and pays a mining fee of 0.03DRK to eliminate change related tracking.
3. DarkWallet Vulnerability : Uniquely identifiable amounts
This mixer is constructed in such a way, where multiple users (or idle mixing bots) are paired up with users desiring to send funds in real time. It’s trivial to de-anonymize any transaction used in DarkWallet due to the unique values of the amounts in the transactions.
For Example:
In this transaction, 0.05BTC was sent through the mixer. To identify the source of the money, one simply has to add up the values on the right until they match one of the values on the left.
0.05+0.0499+0.0001(fee) = 0.10BTC.
0.0499+0.05940182+0.0001(fee) = 0.10940182BTC.
This gets exponentially more difficult as more users are added to the mixer. However, these sessions can be retroactively de-anonymized at any point in the future.
Transactions involved:
https://blockchain.info/tx/4eb3b2f9fe597d0aef6e43b58bbaa7b8fb727e645fa89f922952f3e57ee6d603
https://blockchain.info/tx/1694122b34c8543d01ad422ce600d59f8d8fde495ac9ddd894edc7139aed7617
Solution:
There is no known solution to this issue.
4. CoinShuffle and DarkWallet Vulnerability : DOS attack
Both Coinshuffle and Darkwallet are susceptible to DOS attacks, where a malicious user simply refuses to sign the final transaction or logs off during one of the final phases. Since a signature is required to successfully make the final transaction, this process can be stopped simply by refusing to participate.
Darkwallet and CoinShuffle have suggested a few different approaches to solve this, but all of these allow initial attacks to take place on the network before some action can be taken to protect the network further.
Solution:
Darksend uses a novel approach to protect the network from attack known as a collateral transaction. When opening a new mixing session, the user must make out a complete and signed transaction to the masternode he wishes to mix on. Once the process begins, the user is then obligated to complete the process by responding to requests and completing the mixing session or else the collateral transaction will be cashed. This can be thought of as putting a deposit down on a lease, afterward you retain your money if you acted according to the contract.
Last edited by a moderator:
