eduffield
Core Developer
In the spirit of transparency we contacted Kristov Atlas to ask him to do a review of our technology, Darksend. Shortly after, our community happily crowd funded it and Kristov got to work.
Darksend+ is an iterative improvement on the previous version of Darksend and offers greatly improved anonymity. This functionality is directly built into the reference client for ease of use. Kristov reviewed the technology from every angle to give a thorough rundown of everything we needed to focus on in the future.
What are we trying to fix?
Bitcoin works with an unprecedented level of transparency that most people are not used to dealing with. Every transaction that has ever happened is stored permanently in a ledger that is made public for the world to see, forever.
Darkcoin solves this problem by implementing an ahead-of-time CoinJoin implementation called Darksend. A user that wants to be anonymous can use the built in technology to utilize the Masternode network to make their transaction nearly impossible to track.
How it works, By Kristov Atlas:
http://blog.anonymousbitcoinbook.com/2014/08/visualizing-one-round-of-darkcoins-darksend/
An analysis of Darkcoin’s Blockchain Privacy via Darksend+:
http://cdn.anonymousbitcoinbook.com/darkcoin/darksend-paper/Atlas_Darksend-Analysis-v001.pdf
Yesterday Kristov Atlas published an exhaustive review of the Darksend technology. It’s the most extensive review of Darksend to date. Below is an overview of the weaknesses that Atlas identified.
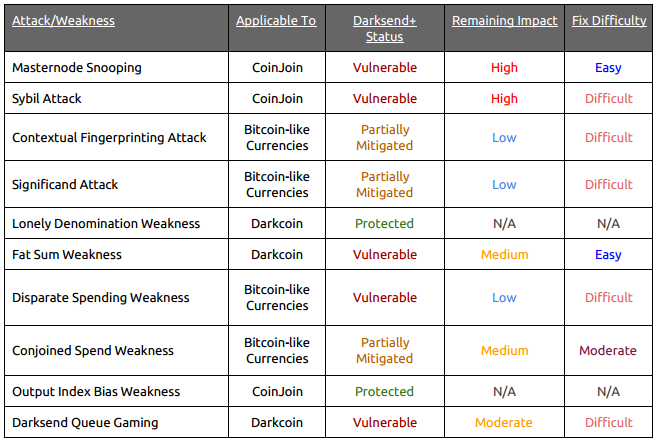
Solved Weaknesses, utilizing Darksend+:
Overcoming these weaknesses was not a small feat, but will be our strongest advantage when competing as a privacy centric crypto-currency.
Sybil Attack
In a Sybil attack, the attacker subverts the reputation system of a peer-to-peer network by creating a large number of pseudonymous identities. This allows an attacker to gain information by observation.
One of the most serious attack vectors found was a sybil attack on a two-peer Darksend denominated transaction. Requiring as few as two peers for Darksend transactions was never intended to be used beyond the scope of testing. As of RC5 this issue has been resolved.
Other sybil-type attacks (such as the active denial to sign) are mitigated by the use of collateral in the core protocol, which is actively used in RC5.
It’s worth noting that Darksend is not the only technology vulnerable to Sybil attack. All peer-to-peer systems have to deal with Sybil attacks, including Bitcoin and Cryptonote currencies.
Masternode Snooping
When Darksend peers mix with each other they use a dedicated node, called a Masternode. This node in the present implementation is required to be able to see the inputs and outputs of the transactions to ensure that parties sign, otherwise the system will charge them collateral fees.
Peers mix with many different Masternodes in a row, known as “rounds” of anonymity in the client. To follow a transaction through the full process, a user must go through a series of malicious Masternodes. This process is random, so a bad actor would need to control many Masternodes in order to attack in this way.
The trade off is a sybil resistant system or one with more personal privacy from snooping Masternodes. But in the case where a Masternode is blinded, collateral protection can’t be used. If a Masternode is blind to the submission of outputs and signing, by definition it would not know who to charge the collateral.
There are other options available, such as banning inputs of users that attempt to break the system. Something like this will have to be utilized in addition to a blinded setup to protect the system from abuse.
Darksend Queue Gaming
This can completely be eliminated by utilizing a provably random Masternode using a deterministic algorithm based on the first user who enters the node, spawning the queue message. A Masternode then could detect the gaming and reject the user eliminating the problem altogether.
Fat Sum Weakness
This weakness happens when someone spends Darksend denominated funds that could not have come from another party.
This is partially mitigated by having three participants per Darksend transaction and can be further mitigated by checking outgoing transactions and asking the user “This action will reduce your anonymity, are you sure?”.
Blockchain Bloat
Darkcoin utilizes anonymity only where it’s needed in the ecosystem. It’s automatically disabled for daemons, so the highest transaction clients will not be creating any form of bloat (Exchanges, Pools and most other high volume clients don’t require anonymity). This will allow the blockchain to grow at a much slower level than our competitors (i.e. cryptonote).
Conclusion
Darkcoin solves the anonymity problem by making the blockchain a fog. There are very few practical ways to attack our system and at it’s core and most of the attacks listed were based solely on the fact that the merged transaction were using only two participants while in the test environment. This has always been a known issue and never was intended to be used beyond testing.
Privacy offered by Darksend can be thought of as a spectrum. Although no technology can ever be perfect, Darksend is intended to provide nearly complete anonymity. The research shows that while discounting the two-peer issues, the anonymity provided by Darksend is strong and will become stronger with further development.
This research shows that Darkcoin and Darksend are maturing technologies and are ready for adoption and use by the general public.
Darksend+ is an iterative improvement on the previous version of Darksend and offers greatly improved anonymity. This functionality is directly built into the reference client for ease of use. Kristov reviewed the technology from every angle to give a thorough rundown of everything we needed to focus on in the future.
What are we trying to fix?
Bitcoin works with an unprecedented level of transparency that most people are not used to dealing with. Every transaction that has ever happened is stored permanently in a ledger that is made public for the world to see, forever.
Darkcoin solves this problem by implementing an ahead-of-time CoinJoin implementation called Darksend. A user that wants to be anonymous can use the built in technology to utilize the Masternode network to make their transaction nearly impossible to track.
How it works, By Kristov Atlas:
http://blog.anonymousbitcoinbook.com/2014/08/visualizing-one-round-of-darkcoins-darksend/
An analysis of Darkcoin’s Blockchain Privacy via Darksend+:
http://cdn.anonymousbitcoinbook.com/darkcoin/darksend-paper/Atlas_Darksend-Analysis-v001.pdf
Yesterday Kristov Atlas published an exhaustive review of the Darksend technology. It’s the most extensive review of Darksend to date. Below is an overview of the weaknesses that Atlas identified.
Solved Weaknesses, utilizing Darksend+:
- Contextual Fingerprinting Attack
- Significand Attack
- Lonely Denomination Attack
- Disparate Spending Weaknesses
- Conjoined Spend Weakness
- Output Bias Weakness
- Blockchain Analysis
- Timing Analysis
Overcoming these weaknesses was not a small feat, but will be our strongest advantage when competing as a privacy centric crypto-currency.
Sybil Attack
In a Sybil attack, the attacker subverts the reputation system of a peer-to-peer network by creating a large number of pseudonymous identities. This allows an attacker to gain information by observation.
One of the most serious attack vectors found was a sybil attack on a two-peer Darksend denominated transaction. Requiring as few as two peers for Darksend transactions was never intended to be used beyond the scope of testing. As of RC5 this issue has been resolved.
Other sybil-type attacks (such as the active denial to sign) are mitigated by the use of collateral in the core protocol, which is actively used in RC5.
It’s worth noting that Darksend is not the only technology vulnerable to Sybil attack. All peer-to-peer systems have to deal with Sybil attacks, including Bitcoin and Cryptonote currencies.
Masternode Snooping
When Darksend peers mix with each other they use a dedicated node, called a Masternode. This node in the present implementation is required to be able to see the inputs and outputs of the transactions to ensure that parties sign, otherwise the system will charge them collateral fees.
Peers mix with many different Masternodes in a row, known as “rounds” of anonymity in the client. To follow a transaction through the full process, a user must go through a series of malicious Masternodes. This process is random, so a bad actor would need to control many Masternodes in order to attack in this way.
The trade off is a sybil resistant system or one with more personal privacy from snooping Masternodes. But in the case where a Masternode is blinded, collateral protection can’t be used. If a Masternode is blind to the submission of outputs and signing, by definition it would not know who to charge the collateral.
There are other options available, such as banning inputs of users that attempt to break the system. Something like this will have to be utilized in addition to a blinded setup to protect the system from abuse.
Darksend Queue Gaming
This can completely be eliminated by utilizing a provably random Masternode using a deterministic algorithm based on the first user who enters the node, spawning the queue message. A Masternode then could detect the gaming and reject the user eliminating the problem altogether.
Fat Sum Weakness
This weakness happens when someone spends Darksend denominated funds that could not have come from another party.
This is partially mitigated by having three participants per Darksend transaction and can be further mitigated by checking outgoing transactions and asking the user “This action will reduce your anonymity, are you sure?”.
Blockchain Bloat
Darkcoin utilizes anonymity only where it’s needed in the ecosystem. It’s automatically disabled for daemons, so the highest transaction clients will not be creating any form of bloat (Exchanges, Pools and most other high volume clients don’t require anonymity). This will allow the blockchain to grow at a much slower level than our competitors (i.e. cryptonote).
Conclusion
Darkcoin solves the anonymity problem by making the blockchain a fog. There are very few practical ways to attack our system and at it’s core and most of the attacks listed were based solely on the fact that the merged transaction were using only two participants while in the test environment. This has always been a known issue and never was intended to be used beyond testing.
Privacy offered by Darksend can be thought of as a spectrum. Although no technology can ever be perfect, Darksend is intended to provide nearly complete anonymity. The research shows that while discounting the two-peer issues, the anonymity provided by Darksend is strong and will become stronger with further development.
This research shows that Darkcoin and Darksend are maturing technologies and are ready for adoption and use by the general public.
Last edited by a moderator:

